While there’s a sense in the electronic market that cloud solutions are new and untried, cloud is built on a mature technology that has been around since the 1960s, when ARPANET allowed users to connect people and data from anywhere on its network. In a very real sense, thoughtfully installed cloud solutions are what original networks were created to do.
IN its most basic sense, cloud computing means delivering computer system resources like storage and processing power, to users on demand. The topologies and management solutions employed to deliver this capability have evolved but the underlying concepts remain the same – this makes cloud solutions more robust, more pervasive, more secure, more widely accepted and more varied than ever before.
According to Genetec’s Christian Morin, the old joke there’s no cloud, just someone else’s computer’ is not a bad way to think about it, architecturally.
“If you remove the factor of the actual physical location of a system’s servers and components, the logic of its topology – the mapping of all its elements, whether related to authentication or any end user services – is very similar whether in the cloud, on-premise or in a hybrid combination,” Morin explains. “The architecture of any cloud system, security included is first and foremost determined by the framework and protocols of the host platform be it AWS, Google, Oracle or Azure.
“Though Genetec is platform agnostic, the global, standardized footprint of say, Azure, provides consistency and predictability from the way we develop our platform, services and microservices to the way they’re installed and deployed. Of course, the cloud provides for a great deal more flexibility related to how quickly a network can scale and how services can be spun up at different tiers and be made available. Another factor is that cloud architectures are newer, and so are closer to the more advanced standards that we are seeing.
According to Morin, many more businesses are implementing cloud models.
“While in the earlier days of cloud computing the inevitability of the shift to the cloud was met with some resistance, today that’s no longer the case,” he explains. “Businesses of all kinds have moved parts or all of their operations to cloud. This has generally followed the standard curve of early adopter to late majority, and the latter is where we now are. The present situation, mandating remote work and greater flexibility has only accelerated this transition, and dramatically at that.
“If we take Microsoft as a bellwether for these things – its CEO, Satya Nadella, recently observed that the company has seen 2 years of digital transformation in this short period alone. It’s fair to say that those industries that are in the categories of mission-critical, data sensitive or security-focused were perhaps understandably more resistant to it over cyber vulnerabilities. But big cloud providers, and I am thinking about Google, Amazon and particularly Microsoft, have done a great job of removing the points of resistance around data security, data ownership etc., inviting security-focused companies to the party and we’re happy to be part of that shift.”

What are your latest and greatest cloud security solutions?
“We began our move to the cloud with our first pure cloud product, Stratocast, our cloud-based video monitoring solution a number of years ago,” explains Morin. “Since then we’ve developed a number of other solutions that were born in the cloud and provided to our customers as software-as-a-service, most notably Clearance, for digital evidence management, and ClearID our cloud-based Identity management system unified with Security Center Synergis.
“These are great examples of the cloud native approach we’re taking with solutions that are really rooted in the ability to aggregate data and access across highly distributed, and most importantly, federated operations. The next step is that we’re looking to make all of Security Center available as a cloud service with the ability to deliver federation on demand via FaaS as well as high availability cloud archiving.”
From the point of view of integrators and end users, getting a handle on the benefits of cloud solutions is important.
“Many of the benefits of cloud are similar, whether you’re an integrator or an end user,” explains Morin. “Deployment is fast so time-to-value on cloud system investments is considerably shorter. It’s much easier to spin up virtual components than physical ones, and this is particularly true in today’s remote and isolated operating environments – deployment is more about configuration than the heavy lifting of loading up boxes, as it has been in the past.
“Once up and running cloud continues to deliver efficiencies, and this is a benefit to all in the ecosystem. But for the end user it means radically reduced IT operating costs. This is the aggregated benefit of having a smaller hardware footprint demanding little to no software maintenance on systems that are always up to date and consume less energy. It reduces risk by ensuring high availability of data across secure and redundant storage in multiple data centres. Of course, it also means having a system that grows with you; one that scales quickly and precisely. You only pay for the services you use and when you need more seats, functionality or space, subscription-based purchasing kicks in to keep it simple and streamlined.
“Specific to the solutions, and again I’m thinking about products like ClearID, Clearance and Stratocast, their cloud-native architectures provide the basis for an array of benefits to users and System integrators alike that I can touch on here. Core to all three is the ability to federate data across multiple internal and external operating entities. For ClearID it means being able to manage trusted identities – the new security perimeter. A good example would be on a college campus where resources are shared between multiple, and even unrelated facilitates with different physical access infrastructure. That means that user identity and privacy can be managed centrally, refined locally, at different points of service and provide a streamlined experience.
“In the case of Clearance, it’s being able to manage ingestion, requests, permission and delivery of highly sensitive digital evidence video content from multiple sources – surveillance cameras, police cams, and public sources, and securely share and collaborate on them. This kind of two-way federation simply wouldn’t be possible without the cloud.”
“Finally, looking at Stratocast, our first cloud product, we’re seeing enormous interest and uptake from companies of literally every size, from the smallest retail locations to massive global organizations,” Morin says. “Three great examples of this are Genetec customers Barclays, Uber and Starbucks all of them Stratocast customers and all of them who speak openly about why their move to the cloud core to their strategy and indeed, an organizational mandate. To quote one of these clients sharing the stage with us on a recent panel, “changing hard drives is so 1990s”. This demonstrates how important, valuable, and disruptive these new technologies are and how Genetec helps customer adapt to changes in the landscape.”
What are the benefits of cloud solutions compared to traditional ways of managing security solutions, according to Morin?
“The list is very long,” he says. “One of the core principals of security is that it is worse to have out-of-date security than no security at all because it gives you a false sense of security. While it’s more of a rhetorical point, operating out-of-data security hardware and software is one of the bigger risks for a network breach.
“Today, as we see a merging of physical and cyber security, running cloud components, not necessarily the entirety of your system, but particularly those that relate to securing edge devices is enormously important. When these devices, and most critically the firmware that run them can be managed and updated remotely and automatically, it greatly reduces the network’s exposure to breaches and malware. I start there not because it’s the most interesting way the cloud serves to advance the management of security, but it begins with security systems and edge devices that are always up to date.
“Another key area relates to identity management – recognized in today’s security paradigm as the new perimeter. Applying the now standard principles of multifactor authentication, single sign on and an increasingly complex services stack in most organizations, the ability to manage users, set and dynamically change permissions spanning disparate systems and facilities isn’t just easier in the cloud, but a game changer. While delivering massive flexibility and efficiency right out of the gate it also opens the door to rapid, painless scalability.”
Morin says that digging deeper into the specifics of physical security across video and access, the cloud offers many interesting advantages.
“On the video side we’ve spoken already about pure cloud solutions like Stratocast, but looking at video management systems like Omnicast, when it comes time to scale ingestion and storage, the benefits of the cloud-enabled environment are quickly evident,” he explains. “For access control, we mentioned the benefits of centralized identity management. Within the framework of a unified security system, combining data from video surveillance and access control is one of the core benefits of Genetec. Applying the flexibility of the cloud, services and microservices that are subscribed to and accessed on demand at once extends an organization’s capabilities but supports operating cost efficiencies that traditional, static, on-prem, perpetual license type systems don’t allow.”

According to BGWT’s Rob Meachem, there are more inquiries in recent times for cloud technologies but they are not evenly spread across technologies.
“Alarms and access control has seen the greatest take up in our experience – video surveillance with its requirement for high bandwidth has been slower to get going,” Meachem says.
“I believe for cloud in the electronic industry, you need to consider alarm and access control separate from video surveillance because of the very heavy bandwidth requirement. What we see happening is a hybrid offering for video where local recording will be the norm and centralised managing will be in the cloud. However, alarm and access control is likely to be mainly cloud-based.
“The 2 main reasons for moving to cloud would be centralisation and management of a site or multiple sites and moving the responsibility of the management of the actual hardware to a better, more secure, entity, or a combination of both. The security industry wants to keep focus on the local assets and the central application can be handled by more experienced IT personnel, as well as moving the expenses model from CapEx into OpEx.”
Salto’s Scott Fraser agrees more businesses are implementing cloud models than ever before – these include SALTO’s latest cloud access control solutions including SALTO KS, a cloud-based access control solution now compatible with SALTO’s XS4 BLUEnet lock range.
“Cloud adoption has never been higher,” he says. “It’s an overwhelming trend for organisations to shift their workload into cloud infrastructure rather than running them in their data centres. Increasingly, cloud native solutions are being leveraged by businesses to do things they simply couldn’t do before or were extremely expensive to do on-premise.
“Businesses are looking to eliminate the amount of infrastructure they have to run themselves as they have to patch it, secure it, maintain it, and keep an expert on hand who knows how to manage it. There are a lot of costs associated with having infrastructure on premise. If you consume a cloud native service or SaaS solution such as SALTO Keys as a Service (KS), then all of that responsibility is with the vendor. Your resources can then focus on the processes of access control rather than system management.”

“SALTO KS doesn’t require any administration effort to maintain or manage. It is always updated with the latest features via instant updates and add-ons. Being cloud-based, there’s no need to purchase software licenses, install and manage complicated and expensive IT equipment, or worry about ongoing maintenance and back-ups. Instead, sites unlock the functionality of their account with a 1-year KS subscription.
“All this makes a cloud-based access control ideal for any organisation with a high turnover or multiple sites with varying levels of connectivity,” explains Fraser. “With a cloud-based security infrastructure, access to every location and every user can be managed from one platform. Updates are carried out quickly too, increasing system efficiency and security, and reducing the risk of human errors.
“Furthermore, with cloud your costs should scale with your consumption. That’s one of the big advantages – you only pay for what you use. You don’t want to have great big servers sitting there waiting for hundreds of users or thousands of access points when you only have 10. Ensuring that you’re able to right-size and grow your platform with your user base is an important advantage of the business model.”
According Gallagher’s Trish Thompson, the cloud isn’t a single solution, but an array of capabilities and value add that businesses can utilise.
“At its most basic, cloud is simply hosting applications in someone else’s data centre and leveraging those economies of scale,” She explains. “At this level, it’s the removal of the need to manage physical, on-premise IT infrastructure for compute or storage but the customer still retains management of tasks like application deployment to the cloud, database management and network security. At the other end of the spectrum cloud is a fully managed and native SaaS (software as a service) deployment which transfers all management of the applications and their availability to the cloud provider. Customers simply purchase the seats they require and use applications delivered over web or mobile that are always up to date. In addition, there are hybrid deployments which have both on-premise and cloud components.”
Thompson argues the security industry can share many of the traditional benefits, drivers, and natural momentum towards cloud.
“In terms of topology, enterprise security systems deploying to the cloud need to think about end to end security in new ways,” she explains. “Enterprise security systems are typically deeply embedded and integrated within the organisation’s infrastructure and business processes. Security systems are also innately designed to manage and withstand server outages while continuing to deliver high availability of security controls on the ground, day in, day out.
“Integrating with systems from on-premise elevators and building automation systems to cloud-based people or visitor management systems, security systems already need to span physical and virtual, on-premise and cloud worlds. De-coupling these components to build a workable cloud topology that is based on the current state of cloud maturity within the enterprise can be a complex task. This means applying a cloud topology to enterprise security is often a journey with way points rather than a single destination. With the cost savings and efficiencies that can be achieved with cloud models and the continued evolution of those solutions in the market, I’d agree that there is an ever growing number of businesses that are seeing value in cloud adoption for their business.”

Thompson says that cloud technologies have allowed the team to simplify configuration and management of Gallager systems with integrator web portals.
“Most importantly, the IT aspects of onboarding our control hardware is now as easy as scanning a QR code,” she explains. “Behind the scenes we’ve implemented full end-to-end security controls and we take care of all the complicated IP networking and addressing that can plague integrators when bringing security devices onto a customer’s network. Our devices can communicate securely over the internet from anywhere and firmware to these devices can be updated remotely from the cloud, ensuring longevity of the customer’s investment.”
According to Thompson, a primary benefit is removing many of the concerns and ongoing tasks that an in-house IT team would traditionally have to manage.
“That ranges from managing the physical environment of on-premise servers including the floor space, air-conditioning, security and access control through to deploying applications and operating systems, managing databases and configuring network security,” she explains. “It’s not that the IT team can’t do these things it’s that they’re time is often better utilised elsewhere. And there are inherent economies of scale in one party providing this expertise across many customers.
“Cloud also mobilises and connects the workforce – again, it’s not the only way to mobilise the workforce but there’s often an economy of scale and resilience that cloud brings. Most importantly, as we see cloud solutions really maturing they will bring the swift feedback mechanisms, the data analytics and eventually the AI that will move security from a more static, responsive and rules-based approach to a very fluid and dynamic “sensing” environment that can more effectively predict potential threats before they occur. This is a longer-term journey which will involve many converging technologies including cloud.”
Thompson says the Gallagher team has recently piloted its fully cloud native solution for small business – Co-Pilot.
“This is a first step in re-imagining a future of security solutions that are customer centric, completely mobilised and focused on placing control and visibility in the customer’s hands,” she explains. “This solution requires no installed software, is always on the latest version and allows small business owners to manage every aspect of security from their phone.
“With Co-Pilot we’ve transitioned to access and alarm control that is securely managed from the phone with simple privilege models. Cards are replaced with more secure mobile credentials that can be issued over the air, from anywhere, anytime. Traditional PIN codes and alarm terminals are replaced with standard on-phone authentication, with the alarm terminal screen transferred to the richer user experience of a mobile phone. Co-Pilot has been designed to work remotely via the cloud or locally over Bluetooth when an internet connection from the phone isn’t available, so availability is assured.
“Co-Pilot introduces a whole new approach to alarms and alarm response,” says Thompson. “Every relevant piece of information from the moment the first alarm occurs is packaged within a live incident report that can be delivered to anyone in the business. That incident includes everything that’s happening on site, the alarm response from those inside the business and the status of external guard call-outs, all in real time. Customers can trigger a guard call-out directly, respond themselves or automate the guard response in advance, all from the app. The incident is soon to include pre and post event video from on-site cameras to help customers and responders make a better assessment of what action should be taken.”

Thompson’s view of the ideal cloud model is holistic.
“With any business model, it’s about the customer experience,” she says. “For myself, that means intuitive, simple and transparent service offerings and the ability to easily modify consumption as internal needs and demands change. Where previously customers might need to grapple with multiple suppliers across a range of hardware items, labour costs, software licenses and maintenance contracts, cloud should deliver a simplified transactional view, couched in language and delivering value the customer intrinsically understands.
“This will drive a need for closer partnerships between manufacturers, integrators and the wider eco-system of security providers to ensure we collectively deliver on that vision. “As a service” models change the incentives from selling highly skilled labour to deploy complex solutions to selling simple, resilient solutions backed by exceptional customer support.”
Ian Law of cloud alarm and automation solutions provider, Alarm.com, says when it comes to cloud business models, integrators should look for partners with advanced security offerings.
“These include things like 2FA, separate passcodes, biometric support for accessing apps, something available for alarm.com end customers via integrators who are alarm.com certified,” Law explains. “This is on top of end-to-end encryption built into the backend infrastructure of a vendor that focuses on these features with dedicated engineers and technically qualified staff. Even products that connect to a platform, like z-wave devices for example, should be tested and certified, something that Alarm.com does.”
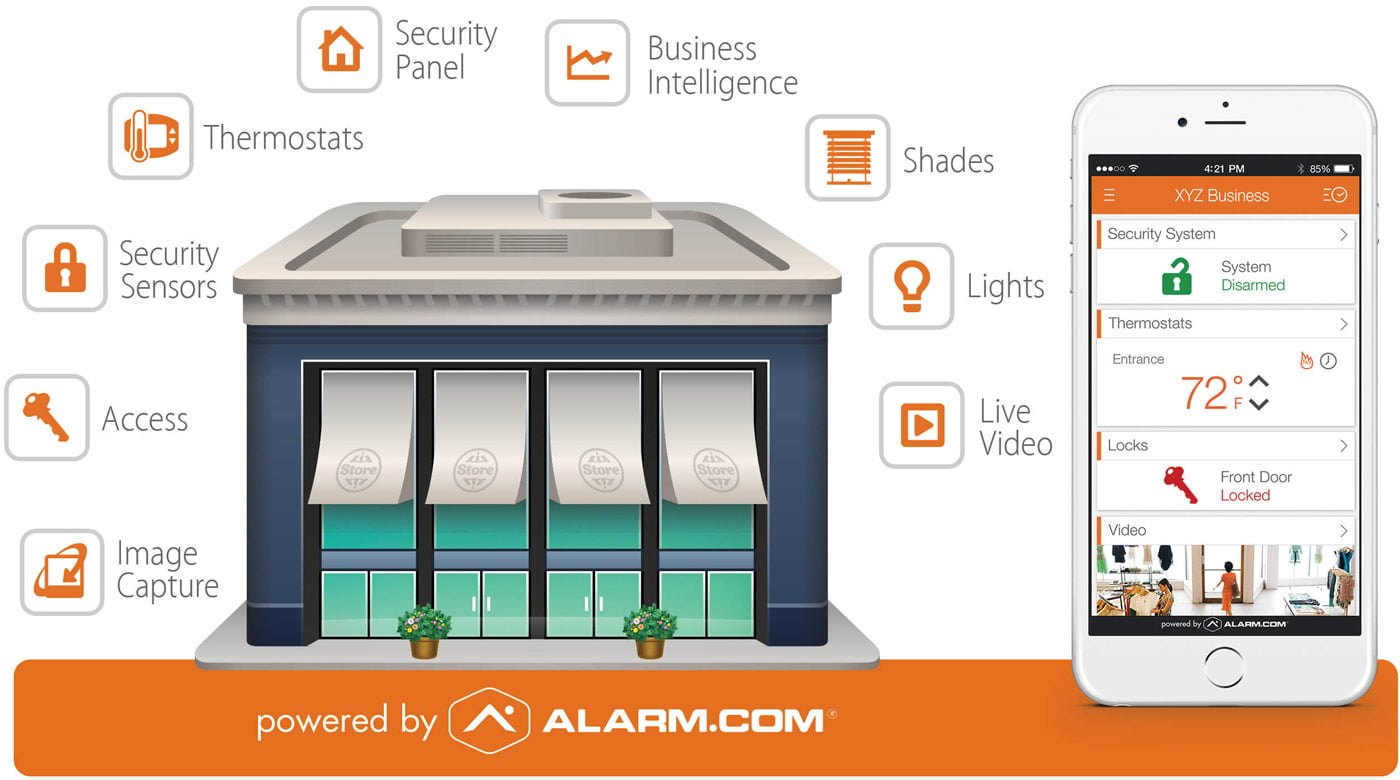
There’s no doubt remote management via cloud adds plenty of flexibility for end users – but how interested in cloud solutions are they?
“Some consumers are tech savvy and appreciate the features built into the solutions like the Alarm.com app – these include features like user code management, multiple site access and management, as well as the reports that can be easily configured to be emailed direct to customer,” Law says.
According to Law, familiarity with cloud technology plays into integrator and end user response to cloud solutions.
“Some customers don’t fully understand cloud,” he says. “For these and other end users and integrators other considerations of cloud include the user experience – how easy and intuitive the app or web interface is to operate, especially when customers are not tech savvy.
“Integrators and installers need to bear in mind that many end users don’t know what a PIR or a reed switch is – instead, they are interested in what a cloud-based security system can tell them. Alarm.com makes it easy for the integrator to make the interface easy to understand with naming conventions that make sense to each individual user and site via an intuitive interface.”
#sen.news










