In what’s now a clear trend, access control systems are changing shape, with remotely addressable solutions like S2 NetBox Quatro, Kantech’s hattrix, Paxton Net2 and Inner Range Inception offer installers simpler installations and end users greater flexibility through remote browser management or cloud support.
ACCESS control is changing – not all at once and at every level but changing nonetheless. A new generation of systems is offering new ways to handle access control and attendant intrusion and automation capabilities. It’s a development that asks users and installers the question whether or not they need to employ a full access control system in a given application or whether or not they can use one of a number of more streamlined offerings.
Important to note, different manufacturers have different ways of handling small and medium sized applications. Kantech hattrix and Risco, are cloud-based solutions, with some aspects of the access control process managed in proprietary cloud. Other systems, such as Inner Range Inception, employ browser management of local controllers in which databases and event logs are stored. Regardless of which system topology is being employed, one thing is universal – a push to simplify installations, reduce the cost of smaller solutions and give installers and end users greater flexibility when it comes to maintenance and management of systems.
Something else that’s common in this part of the market is that systems don’t require licensing and there’s an element of plug and play to their installation. Once a controller is set up on a local network and the management software is installed on a local workstation, the software will find and enrol the controller, as well as readers and other devices. From the point of view of installers, putting systems together into a coherent whole is much simplified with these systems, with doors and inputs assigned to areas, users granted authorisation to areas and aspects of automation created and populated with input and output devices.
A great strength of these systems is that they are remotely addressable for maintenance and management and there’s no doubt this contributes to their functionality considerably. There’s a level of intuition that applies to a system that can be monitored or massaged into better shape remotely – users can check out events and register new users, while installers can handle maintenance without wasting 2 hours in traffic.
Appliance-based solutions are essentially out of the box – you slot them into a network and they are good to go for the majority of access control solutions installers might need – systems with up to 8 doors and 16 alarm inputs. Not only can these systems handle alarms and access control, they also bring in CCTV and offer real time event logs with video associated alongside. That’s seriously attractive for any integrator, not just learner installers branching out from the safety of wireless alarm panels.
Depending on their configuration, a typical traditional access control solution might have a control module, a TCP/IP module to allow the controller to communicate with a network and a PC with software the TCP/IP module can communicate with. But these sleek new solutions allow installers to simply plug their controllers into a network then browse an IP address via laptop (or run a software tool that does this job for them). With the controller found, they can browse in and configure and manage their system in a seamless and intuitive way. No Windows, no integration, no servers, no dedicated workstations, no licensing, no anti-virus to configure, not firewalls to negotiate and none of the endless patching. No it’s not for everyone but it’s just perfect for many SMEs.

Cloud-based solutions can offer something slightly different, depending on the needs of the user and the business model of the provider. Kantech’s hattrix is an example of this. EntraPass is the software that drives hattrix and end users can manage their access control system using an EntraPass equipped workstation, or they can have the provider manage the system for them and only interact with readers and/or keypads at their offices. System management, including enrolling staff and keeping an eye on system or network events can be handled by the provider directly or outsourced to a professional monitoring station.
A big advantage of a cloud solution is that it requires considerably less investment in hardware. For instance, with a managed Kantech hattrix service, the provider hosts the database, server applications and infrastructure, as well as providing the initial set-up of the account and onsite controllers and devices. With everything good to go, the end user can manage the system from a secure web client or workstation. Instead of paying for the hardware and setup as an upfront cost, the user pays an ongoing fee. Cloud-based solutions like this are more mobile than traditional systems because the user can take their service with them. With much of the hardware, including the database server in the cloud, smaller organisations can move between locations without the need to completely rebuild their access control and security solutions.
For the end user, hattrix offers an intuitive and secure WebStation which includes animated graphics, email reporting live events viewing and more to enable end users to remotely control their own security management tasks in real-time over the web for a hosted approach, or turn over some or all security responsibilities to a Managed Service Provider (MSP) for a hybrid or fully managed solution. There’s also no need to employ dedicated staff to support the system. Same as the other systems here, the hardware component of hattrix has plug and play connectivity. A technician just plugs the controller in and there’s secure communication using Ethernet 128-bit AES 3DES encryption for remote configuration by the provider.
The key things with hattrix include the elimination of network and computing infrastructure capital costs and ongoing operational expenses such as database/operating system upgrades, hardware replacement, anti-virus software and networking equipment. Removal of training and system management. The end of maintenance inefficiencies – the user pays for a complete service and the responsibility for making it work rests with the provider – including backups, redundancy and data security.
Comparatively, S2’s NetBox Quatro is a network-based solution that combines alarms, access control and video surveillance functions like Forensic Desktop, in a browser-based environment. The strengths of this solution are its simplicity, ease of installation, accessibility and its ability to bring together multiple remote systems locally or anywhere in the world.
Management of the S2 NetBox VR Quatro is handled by a combination of the S2 NetBox enterprise-class security management system (SMS) with S2 NetVR, a video management system (VMS). Operationally, Quatro’s basic system supports 4 IP cameras and 4 doors with expansion to 8 cameras and 8 doors. The internal 4-slot card cage takes standard S2 blades and these include access control, supervised alarm monitoring, relay output control, and analogue temperature monitoring.
Importantly, the program and system data (it’s robust Linux Ubuntu) are tucked up on a non-volatile SSD, while cameras are recorded on an internal hard disk (1-3TB). This big capacity gives 30–90 days storage depending on resolution and frame rate. S2 NetBox Quatro is happy as a stand-alone system where it supports SME sites or bigger domestic applications. But there’s more to Quatro than meets the eye. Its open architecture means that any S2 system is a finger-snap away from being part of a global security solution with none of the complexity or expense typical in client-server architectures. That’s the beauty of a browser-based architecture.

In the flesh, S2 NetBox Quatro is a well-proportioned aluminium housing more square than rectangular. The box has plenty of breathing space knuckle room and knockouts. Inside are the network controller, an access control module and room in the box for another 3 modules. These can handle 2 full portals (that’s 2 readers, 4 inputs, 4 outputs), 8 outputs or 8 temperature points.
Quattro is a thin client – a network appliance – and all it demands is power and a Cat-5/6 drop cable to a network switch. On the inputs side, you carry IP cameras into the video modules in the usual way and alarm inputs into the alarm input blades. Same with readers – they arrive at Quatro on Weigand runs. Once this is done you simply go to any workstation and browse an IP address. If you’re trying to imagine S2 NetBox VR Quatro conceptually, picture a single case with the server board, reader blades, alarm input/output blades and storage bins all onboard. Now picture yourself somewhere on a LAN or WAN browsing into an appliance through any workstation or mobile device.
When it comes to the management side, there’s no Windows software, licenses, servers or third-party HLI torture. And because it’s browser-based, no matter which OS you run, Mac or Microsoft, you just step right into the system and get to work. And S2 uses core software technology from Exacq Technologies, so around 1000 cameras are supported. Performance on the video side is solid, with S2 NetBox VR Quatro delivering 1-25 frames, and compression and bandwidth options selectable depending on camera set up. Not surprisingly, there's a mobile app for video and access control.
Another browser-based solution is Inner Range Inception. This system has 4 doors onboard with LAN expansion to 32, 8 SIFER readers onboard with expansion to 64, expansion for 32/64 Wiegand readers, 32 areas, 8 alarm inputs (LAN expansion to 512), 4 outputs (LAN expansion to 512), 2000 users and a 50,000 event log. The system is supported by the Inner Range–Paradox RF module and RF devices, and local control is via the compact Elite LCD keypad.
With Inception, there’s no licensing – you simply buy the product and install it and the fact there’s no dedicated software because there’s a web interface contributes to the simplicity. Importantly, Inception uses a lot of Integriti modules, including the 8-zone expander and the 2-door access modules. If you want more doors you buy more SLAMS, in you want more inputs you buy more 8-zone expanders and you choose different housings to suit the number of expanders you need.

Inception’s Commissioning Checklist allows installers with very little experience to create an access control system while at the same time gaining a strong understanding the underlying nature of access control solution structure. You start off configuring network settings, date and time, network settings, move on to configuring system settings like EOLs, areas, doors and users, and you end up creating automated events and setting up monitoring paths.
Another solid performer when it comes to browser-based access control is Paxton’s Net2 controller. Features include 2 reader ports and 1 intruder alarm port and relay, RS485 Dataline and TCP/IP communications, 2 voltage-free relays, support for Paxton and third party 12V DC readers and switchable termination resistors with LED. Net2’s software is extremely easy to use and allows very simple setup of small or bigger systems.
Once the controller is registered, readers are automatically assigned and once users are in the system you can assign them to doors, or all doors, automatically or with a click. From adding users individually or as a database, to selecting tokens and applying access rights, Net2 is intuitive in layers. When we reviewed a Net2 recently we loved the way the system automatically found components for the installers to designate, and we loved the way the access to the system’s functionality was made available no matter where you happened to be in the software.
Fundamentally, access levels are a combination of a door and a time zone. With Net2 plus, you simply create a time zone and then select it when setting up doors. Once the time zone has been created it’s always there to be selected. I’m set up for all day every day but you can play with this ad infinitum. The same thing applies to holiday schedules.
Triggers and actions is a strength of Net2 and it allows use of events to drive a complex local or remote response. Events like double presentation of a valid token, arming of the alarm system, when the keypad doorbell is pressed, when an ACU goes offline, when a fire alarm goes off, when a keypad is hacked, when a battery fails and loads more, can be used to drive actions. These actions include things like, play a file, send a text, email, control a lockdown, drive a relay, and allow temporary access. When it comes to driving relays, you can select turn off, turn off, turn on for a selectable period of time.
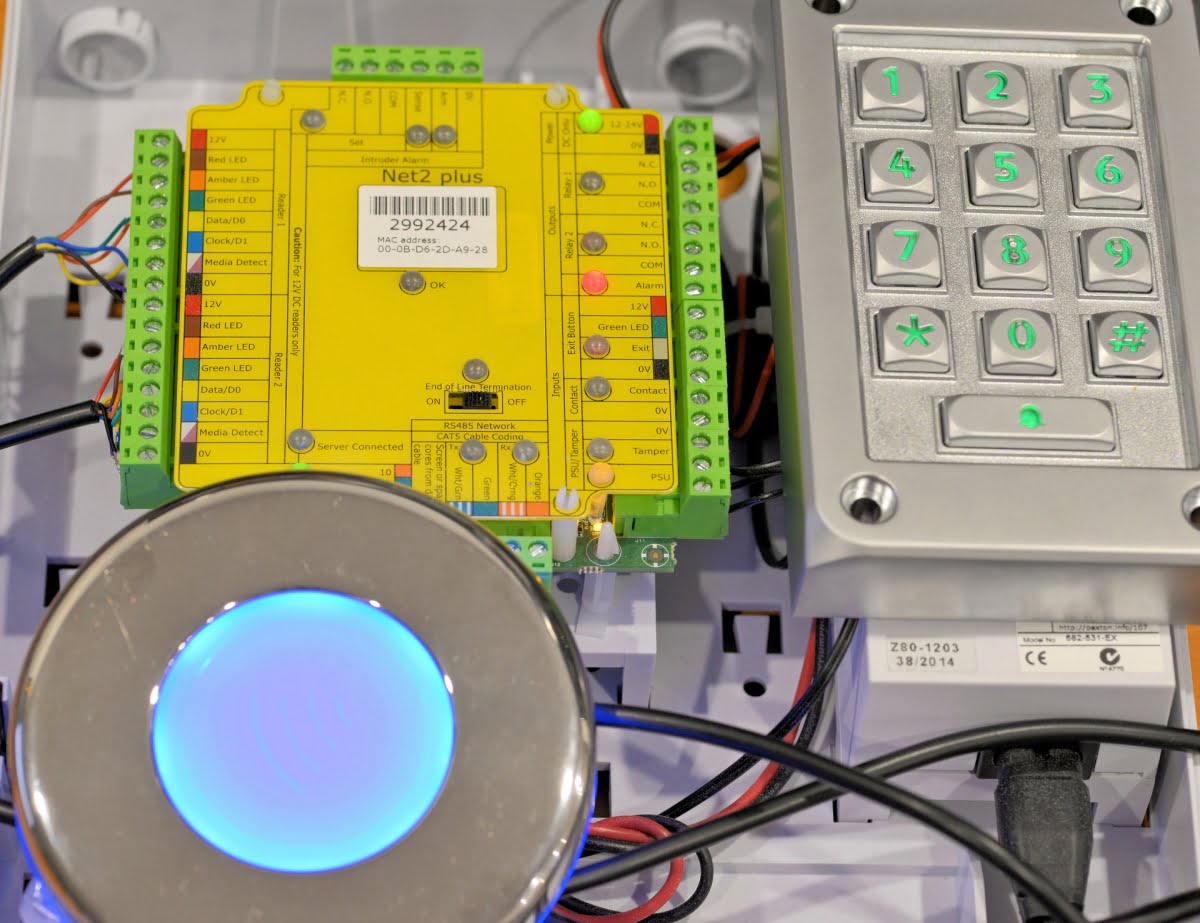
There are also comprehensive reports that can be generated based on users, tokens, event times, who is in the building right now, who has clocked in during the day, last known positions, first and last events and many more. All these, and everything else about Net2 plus software programming, is designed on the basis of long experience, to offer installers and users a selection of those functions they are most likely to need.
Another great capability with S2 is camera integration. Again, it’s very simple. You find an NVR on the network, slot in the IP address and the system will populate that area with the cameras from that NVR. You can also associate doors with cameras and the system automatically populates the door with a little camera icon underneath which is video anytime you click on an event involving that door.
Conclusion
You could argue that these sleek access control solutions herald a metamorphosis in the way alarms and access control (and CCTV) solutions are managed and installed. They are browser-based and/or app-based (there’s an app coming for Inception) and what sets them apart is the simplicity and power of their interfaces to govern inputs and outputs. In each case, considerable engineering has gone into streamlining the process of installation and management and when you’re installing, configuring and driving any of these systems, that’s the first thing you notice. It’s very easy to do.
Is it the end for traditional access control and intrusion panels? Will there be a time when it’s considered very last century to program and manage a quite complicated security system using nothing but an LCD keypad necessarily supported by a dedicated workstation? For smaller solutions, yes, for sure. These new solutions enhance installers’ ability to express the power of access control, intrusion detection and automation solutions; as well as extending an end user’s capacity to exploit it.
By John Adams