What are the challenges, benefits, requirements, skillsets, management options, expectations, vulnerabilities and topologies of enterprise access control solutions? That depends on your perspective.
Enterprise access control is a challenging process that demands careful planning, excellent knowledge of products, as well as rock-solid ability to specify and provide underlying infrastructure. Adding to the complexity, enterprise access control solutions are often the hub around which key subsystems rotate – that can include automation, lift control and the toughest system of all, enterprise CCTV.
Making things more difficult is that the challenges, benefits, requirements, skillsets, management options, expectations, vulnerabilities, and topologies differ depending on which stakeholder angle enterprise access control solutions are viewed at. What’s most important for an integrator is not going to be what’s most important for an IT manager or an end user, and when you throw variations in networking infrastructure and remote application, things get more complicated still.
While it’s possible to argue enterprise access control is modular and made up of a series of remote systems that can be centrally managed, in practise these things are never so simple. Very large sites are organic in their evolution, defined by their technologies and restricted by their budgets over time. Trying to make sense of all this across multiple sites is never going to be easy.
From an integrator’s point of view, what are the biggest challenges of enterprise access control systems? According to Innotec’s Rob Rosa, there’s much more to it than meets the eye.
“If you are talking from a retrofit as opposed to a greenfield site, the complexities range from current cabling infrastructure, integration requirements of current devices in place, card technology utilised and new requirements/features to be integrated into the new platform,” Rosa explains.
“Sites with multiple and separate systems being used for example standalone CCTV/VMS platforms, intrusion detections systems, perimeter detection systems, thermal requirements, etc, can be a challenge, given that sometimes older systems do not integrate into new systems, but a good integration company can provide a solution to many of these challenges.
“In a greenfield site, the fact that requirements can be taken from a clear and concise security plan as to what you wish to achieve allows you to put in a modular system that has high level integration into numerous platforms or dependant on the enterprise system, the major platforms already are very powerful and can provide numerous functions and futureproofing for the security manager and what outcomes they wish to achieve.”

What characteristics do integrators most value in an enterprise access control solution – what can’t they do without? Rosa leans towards customer requirements.
“ From my experience, what clients are looking for is flexible and module system which delivers the user the ease of use, can expand and grow this the clients requirements and provides huge range of flexibility in relation to 3rd party integrations such as car park solutions, locker systems, payroll, OHS and the obvious like alarm and video integration,” he explains.
“It is a long list, but technology advances are pushing this list of most value characteristics way beyond what would have been a wish list a few years ago. The most important aspect of then delivering on the above is how the platform you are going to implement will continually improve as far as the manufacturer continuing to develop, improve and ensure that fixes are pushed out for the small bugs in the systems.
“In essence, flexibility, open platform (true non-proprietary systems), integration into 3rd party field devices and systems and the ability for another integration company to walk in and take it over so that you are not locked in, are all important aspects of a strong and reliable access control system.”
A challenge of access control systems can be cabling large sites, and this has led to the growth of highly flexible wireless solutions. Can such systems be incorporated into enterprise access control systems?
“Wireless systems provide the integrator and the end user with ability to expand access control coverage to areas that in the past may have not been possible or feasible,” Rosa explains. “The wireless devices provide coverage to many hotel and student accommodation facilities and provide a good layer of security in these cases. It provides a high level of security without the wiring constraints and these days the battery life in many of these devices last a few years (depending on usage, etc).
“However, as we move into high levels of security requirements in buildings and multi-site configurations, another layer of complexity and functionality is required which in my option requires a server based management system to provide the overall arching flexibility and control that the wireless system cannot do. The wireless solution is a great addition to any system enterprise but I believe this needs to be part of a total package which includes a server-based management system to bring an enterprise solution together.”

Do customers ever request Innotec create an enterprise access control solution from multiple existing systems – what are the challenges inherent in this approach?
“We have been asked numerous times to integrate multiple sites that operate different systems,” Rosa explains. “Sometimes it is possible and other times it is not. It will depend on what readers and cards are being used on these sites, what devices can and can’t be integrated or if a separate SDK may be required in order to make it work and then there is the potential to implement a 3rd party umbrella software but again, all site specific and also age dependant on the current systems.
“We find that some people have very old systems that have not been maintained from a software (and hardware) perspective, then customers think we can just upgrade it the latest version of software and everything will be fine. The fact that hardware may not be able to deal with the newer software version, etc, is only a small piece of the puzzle and this why it is imperative to get a full site survey done to ensure a comprehensive understanding on what’s installed on all sites before making any enterprise recommendations.”
According to Andrew Zafra, solutions like UTC’s C4, which provides an umbrella for Tecom’s whole range, as well as any third-party systems imaginable, lend themselves to enterprise applications.
“C4 takes in all the features of the Tecom product range, and the third-party range is ever increasing,” he explains. “There are new integrations that are being released and more are on the roadmap as TecomC4 creeps through the Australian market. The latest integrations that have been released are Keywatcher, Traka by Assa Abloy and Digifort.”
What lessons did installing C4 enterprise access control system throughout all Hills’ branches and sites around Australia a couple of year’s ago teach the UTC team?
“The way the company structure was originally planned didn’t really work for us,” Zafra explains. “The best thing about discovering this was that the system could be redesigned without causing disruption to the application. You could just build the new structure in parallel with the original and then move the people to the new structure. This made the migration to TecomC4 easy with a basic understanding on how the system functions.”
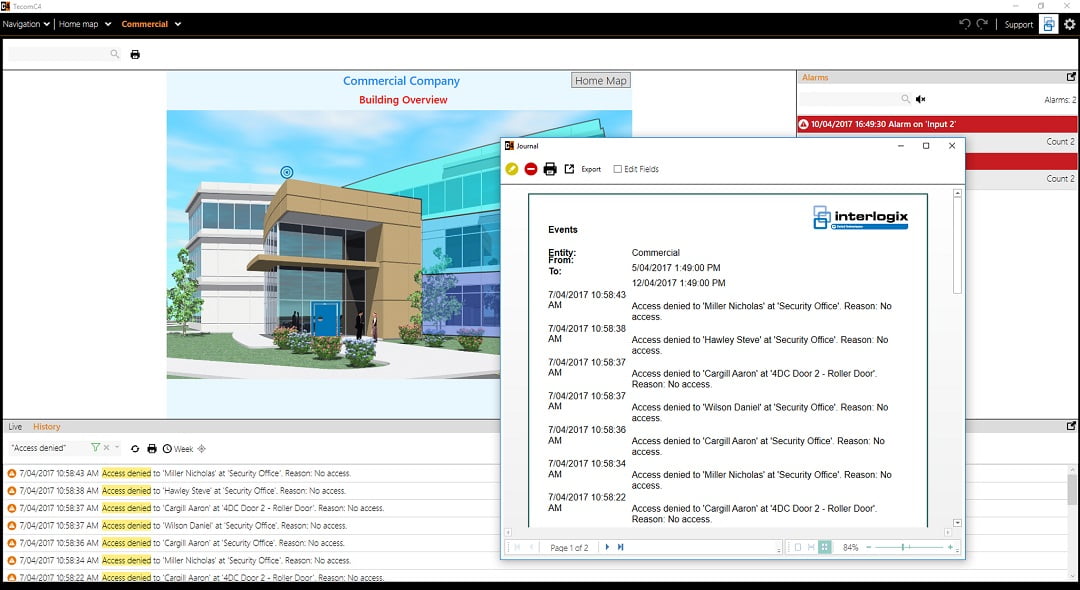
According to Zafra, the most important pieces of functionality delivered by an enterprise access control system include fundamental like ease of use, credential management and integrations providing the user facility and security management in a single interface.
“The intuitive event log is critical, I use it to check when alarms have occurred at remote sites to ensure a staff member or cleaner had been onsite,” Zafra explains. “The mapping is very important for sites with a turnover operator staff (Guards) as it gives them a better idea of where the alarms or events are happening.”
According to Inner Range’s Russell Blake, there a number of skillsets required by enterprise integration teams and they are not always what you’d expect.
“One of the key areas to achieve success is interpreting, communicating and setting realistic expectations between all parties,” Blacke explains. “When the team is clear and focussed, amazing results can be realised.
Inner Range’s Steve Mitchell agrees integration teams need a wide range of skills which can vary considerably from project to project.
“Above all they need a member in the team who not only understands what is needed when integrating different systems but can effectively communicate those requirements to the relevant parties,” Mitchell explains. “Inner Range also assists in this process with our Enterprise Account Management team by providing a bridge between the varied stakeholders involved in the integration of enterprise level systems.”
What are the greatest challenges of successfully implementing an enterprise access control solution according to Mitchell?
“It’s essential that the specific requirements of the customer are known as early as possible so the correct system architecture and required integrations can be planned from the onset of the project,” he says. “Receiving previously unknown customer requirements at the commissioning stage can result in the project running over time and budget due to the changes which may be required. In worst case scenarios changes in architecture and additional hardware or software licences might be required.
“It’s also important to partner with an access control manufacturing company that specialises in quick, agile and local custom engineering. This service needs to be easily accessible through standard professional services. Changes will come with any project; it’s about having the peace of mind for the integrator and end-user knowing the manufacturer is in it for the long-term.”
Enterprise access control solutions typically involve integration of multiple systems across multiple sites and whether this involves a level of customisation depends on the supplier.
“Inner Range has over 100 existing inhouse developed integrations and an R&D team that can quickly and cost effectively deliver new integrations on a per project basis,” explains Inner Range’s Mark Cunnington. “It has been the responsiveness of the Inner Range R&D integration team that has been a critical factor driving our rapid growth in the enterprise segment”
“If a customer does not take advantage of the integration capabilities available with enterprise access control systems they are missing out on a major benefit,” Blake agrees “The ability of the modern day access control systems to integrate to 3rd party systems such as payroll, CCTV, active directory, number plate recognition, lighting systems, home/building automation systems, asset tracking systems and many more 3rd party systems sees the access control system become a central point to connect multiple 3rd party systems together which gives the customer unprecedented control over security as well as the convenience of business process automation.
Ultimately, all of this sophisticated technology is about giving the end-user what they want – more bang for their buck.”

Should an enterprise access control solution include video surveillance to enhance remote situational awareness – if so, what’s the best way to express video streams in a management workstation, according to Blake?
“Enterprise access control should definitely be integrated with any video surveillance systems which are installed on the site,” he explains. “After over 20 years of experience in enterprise access control Inner Range has found that systems need to be as simple as possible for the operator to use. It is essential that CCTV and any other integration can be intuitively used through the Access Control interface. Ideally cameras should be able to be accessed from multiple places such as from a clickable icon on a map, when controlling a door, when viewing the log and when controlling a third-party integration.”
You’d expect an intuitive event log and site mapping to be even more important when it comes to remote management of multiple sites and Blake says it’s the key.
“An intuitive interface for any part of an enterprise access control system is more than important, it is essential,” he argues. “This applies to any sized system no matter if it is 1 door or 10,000 doors spread around the world. An event log may need to be used when tracking an active breach of security so must be extremely quick and easy to use and be capable of providing information which can be used to make quick decisions in high pressure situations.
“Mapping is also important in these situations as it enables an operator to easily monitor a live security breach while easily viewing integrated CCTV Cameras to verify there is nobody in the area followed by locking down areas to contain the security risk.”
Meanwhile, Mitchell says a true integrated security management system will orchestrate and empower the security operation team.
“The SMS is there to automate alarm processes to facilitate the delivery of the exact amount of information in the exact time (e.g. video popup to verify alarms),” Mitchell explains. “Functionalities like vector-based maps, vector-based animations, automatic drill-downs, automatic notifications and more, are now expected as standard features within an enterprise access control system.”
Access control technology doesn’t stand still – even less for enterprise solutions, which drive over rapidly evolving networks. In this environment, are local server-based architectures going to give way to virtual server-based solutions in enterprise applications?
“The benefit of virtualisation is far reaching, but certainly not just for access control solutions,” says Gallagher’s Mike Margrain. “Virtualisation typically makes it easier to make a solution highly available whilst introducing improved server monitoring and general management, with a more effective way to increase resources as a system needs to scale.
“Guest VMs share resources from a host machine, which typically has high performance hardware that is replaced more often than on a standalone server. This means that systems today are more reliable than they used to be. For access control, when coupled with more robust operating systems, this often means server level system interfaces are more popular than in years gone by.
“This is because server/PC level interfaces typically provide for better logging and testing, which makes troubleshooting easier if something goes wrong. Interfaces and integrations can provide significant benefits but always introduce complexity and risk to a system. Anything that can be done to help reduce those risks or identify and resolve problems is generally a good thing.”
Margrain agrees that an intuitive event log and site mapping is vital when it comes to remote management of multiple sites.
“It’s important to provide helpful information to operators when dealing with incidents,” he says. “This is especially true when response time is paramount—such as when dealing with critical infrastructure assets or when personnel safety is involved. Not all operators always have intimate knowledge of all sites, so presenting information and functions to them in a context-sensitive manner goes a long way to ensuring they can respond quickly and also respond well.
“If an event is raised, we will only present information that relates to that event. This means the operator has everything they need to make an informed decision about what to do next. This could include live status, graphical map views, recent history from the item (and items near that item), useful override links, and alarm instructions which might contain standard operating procedures set by the organisation.
“We put lots of R&D effort into the user experience within our Command Centre client—going to great lengths to reduce cognitive load on the operator and improving response times by minimising the need for superfluous mouse clicks, for example,” Margrain explains. “This extends to having a flexible client which can be tailored to a given organisation, a site, or even a specific operator sitting in front of it. Privileges and layouts can even change based on the location that operator logs into the system from.
“Having the operational client adapt to the person using it means lower training overheads and more confident operators—making for improved site operation. This is especially important for large multi-site systems.”

Something about enterprise solutions that’s often not appreciated is how they are expected to scale, globally. For the uninitiated, the scaling can be vast, taking in hundreds of sites around a nation or around the world.
“Having pioneered native IP peer-to-peer access control devices, scale is an area Gallagher has always excelled in,” Margrain says. It’s not uncommon for our end-user systems to have thousands of access-controlled doors, hundreds of thousands of cardholders, and hundreds of workstation operators. These systems might span large geographical areas (i.e. interstate or international) and could also employ multi-server mesh architecture to retain autonomy when site-to-site communication is lost. Providing a scalable networked solution that is robust and secure from the very first controller is one of the top priorities of what we deliver to market.”
It’s not all about integrators and suppliers. What do end users expect from their enterprise access control solutions – what are their operational goals, generally speaking? According to ICS Group’s Scott Myles many customers’ demands are rapidly evolving to meet new challenges and threats.
“The traditional requirements for an enterprise access control solution have been centred around secure access management and the control of assets, with automated functionality (integration) with supporting solutions such as CCTV and BMS,” Myles explains. “In most circumstances our clients are looking for a layered single card solution that can be easily implemented across their entire portfolio with unified credential management with Active Directory, and simplified processes when it comes to integrated alerts and reporting.
“However, due to the Coronavirus, our clients goals have changed to not only the protection of assets, but to the protection of people, as shared buildings and public places have now become high-risk environments for the spread of diseases such as Covid-19, and as electronic security designers we soon realised that we needed to have a fresh look at the way we designed our solutions.
“In meeting our client’s expectations, our design strategies are now centred around zero touch,” Myles says. “As security professionals, we believe that technology will play a vital role in meeting this challenge and solving these issues and our zero touch design strategy goal is to allow our clients to navigate and access their place of work (work bubble), without the need to touch doors, readers, intercoms lift call buttons whilst still maintaining the same level of security controls.
“The unification of multiple systems and centralised management has great benefits from a corporate perspective in reducing costs. A centralised approach allows the organisation to holistically manage and monitor their sites without the need for site-specific infrastructure or additional personnel.
“From a centralised monitoring point of view, having detailed site maps and event logs that provide icons and real time alerts with supporting video is essential for operator’s understanding of current activities, as well as post event analysis of events through loss prevention investigations,” he explains. “In addition to event logging, applications that bring multiple systems into a single interface to provide enhanced evidence management is beneficial when faced with the increased demand when monitoring multiple sites.”
What’s the most difficult thing about designing an enterprise access control system from the point of view of a consultant?
“Traditionally one of the most important things in designing an effective solution is truly understanding the client’s security vulnerabilities and how the organisation operates,” says Myles. “You need to take into account all the various operational workflows of staff, customers and contractors and how each defined group will need to be identified, and the different levels of access required depending on their group or their role.
“In the design process I like to map this out to understand the various groups within an organisation, and then start looking at how these groups being people and vehicles move through the facility, taking into consideration elements such as entry doors and gates, vehicles and parking facilities, general public areas, back-of-house areas and any sensitive areas that require a higher level of protection such as data rooms or high valued assets or for a hospital’s drug cabinets, etc.
“With ‘Zero Touch’ now front and centre in the design process has seen the inclusion of technology such as electromechanical hydraulic door operators that automatically open and close doors when activated, removing any human intervention. The devices are suitable for almost all types of internal or external swing doors and the process is simple, access is granted via long range card readers, and egress depending on the access level can be the same or via a touch free request to exit button.”
According to Myles, another area of complexity ICS Group is finding, is meeting the client’s vertical transport requirements because the traditional means of access via lift call buttons or via destination lift touch screens controllers requires a level of human intervention, either in the lift car itself, or in the lift foyer.
“This is where zero touch can play a role through integration of access control with destination lift controllers, to allow the user’s credentials to select the required level through the use of long range card readers positioned in the lift foyer, instead of manually operated panels or touch screens,” Myles explains. “This may be difficult for existing sites and depends on the current lift infrastructure, however, with new sites and up-grades, this level of zero touch operation is becoming commonplace.”

What’s the typical architecture of an enterprise access control system? It varies, depending on what networking technologies are available that can support a solution.
“Defining the architecture of an enterprise access solution can be answered in 2 ways – the physical system architecture or the operational functionality of the system,” Myles explains. “As most of the audience may be aware of the physical requirements such as master controllers, door controllers and the various in-the-field devices, I’m staying with the functional architecture and the complex relationship between the user and administration requirements and the various levels of operation here.
“From a management perspective the system management software should be capable of being a single overarching platform for the programming and administration, control and monitoring of all the in the field integrated access control and intruded detection devices. Ideally the system should support identity management, credential management and access management that provides enterprise governance through auditing and reporting and the ability to federate within the organisation portfolio.
“The various architectural layers beyond the core components should include integration and synchronisation with Active Directory to automate the enrolment processes, providing opportunities for simplified credential management and user access levels. Other layers or applications such as alerts and monitoring, with alarm events that display on dynamic interactive maps are certainly beneficial with the ability to push alerts to off-site monitoring centres or use of mobile and Web-based client apps. In relation to systems unification, connections between multiple sites through cloud support services essentially create a single virtual system to allow global credential management creating a multilayered but single card solution.”
Given the complexity of their topologies, you’d expect that there can be vulnerabilities when enterprise access control systems are not well designed.
“Enterprise access control solutions can have extremely complex digital infrastructures and footprints, deployed over many sites and assets, spread out over cities, nationally or in some cases different countries,” Myles explains. “With this level of complexity, from client on site workstations through to remote system managers may leave systems vulnerable to internal or external actors gaining access to systems or parts of systems, either compromising security through the release of doors or as a method of obtaining ransom, due to infiltrating and having control of the solution. Having good IT practices and governance in place is essential to reducing the client’s exposure of these risks.”
#sen.news









