Nozomi Networks Finds Vulnerabilities In Axis License Plate Verifier – Axis Releases Patch.
Vulnerabilities In Axis License Plate Verifier – Nozomi Networks has undertaken security research activity focused on the License Plate Verifier software product offered by Axis Communications.
The Nozomi analysed Axis License Plate Verifier application software on an Axis P3245-LVE-3 camera and has discovered 6 vulnerabilities that affect the License Plate Verifier application version 2.7.1 (latest release at the time of the analysis) installed on all compatible Axis devices.
These issues could allow an attacker to exfiltrate credentials to access additional systems, elevating privileges to reach forbidden functionalities and gain arbitrary code execution with full privileges on the device. Nozomi Networks Labs notified Axis in May 2023, and it responded by sharing additional details together and a timeline for updating the License Plate Verifier application.
Each Axis camera can be managed through a dedicated web interface running on the Linux-based device, allowing the user to configure many different settings, including network or security settings, and users and credentials.
For security purposes, users with access to the web interface are divided into 3 groups:
- Administrators: Full access to the system and its settings.
- Operators: Full access to the system and its settings except for user creation and some other specific limitations.
- Viewers: Very limited access to the system. By toggling a specific option, viewers can be set as guests, requiring no authentication.
Meanwhile, the Axis License Plate Verifier is an additional web application that can be installed on compatible devices through the Axis main web interface running on the device camera. On some specific Axis products this is installed by default.
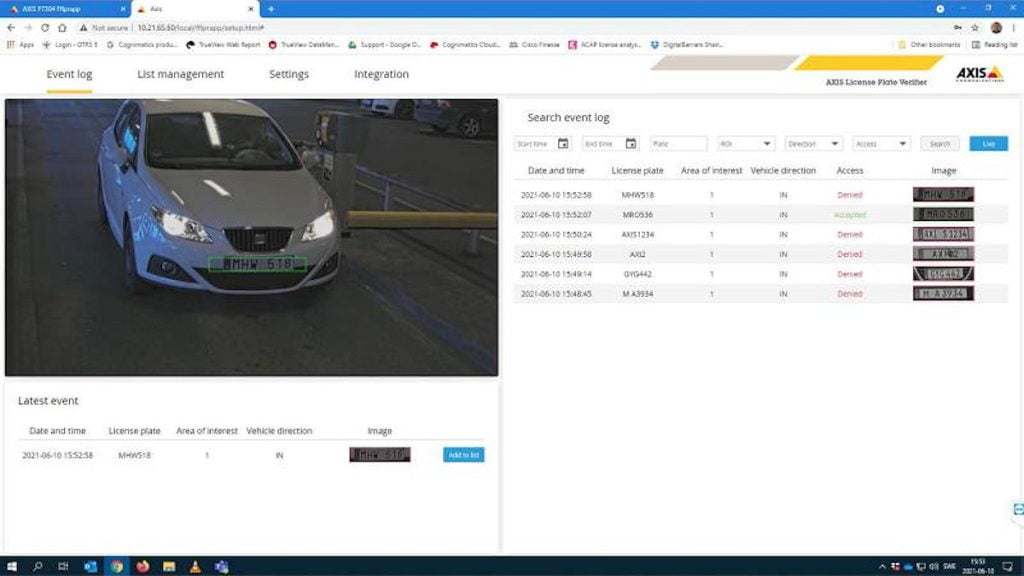
The application allows the creation of customised access rules based on the recognition of license plates detected on cars that transit through the monitored area. Additionally, multiple cameras can be linked together to share the same access control rules on different monitored areas.
Further, multiple cameras can be linked together to share the same access control rules for multiple monitored areas. This functionality called ‘camera synchronisation’ requires the insertion of the camera’s IP address to be linked, together with a username and password valid for each camera to be synchronised. The credentials are required to correctly authenticate the cameras that the user wants to synchronise, and they need to belong at least to the operator group to authenticate correctly.
Vulnerability Analysis: Axis License Plate Verifier 2.7.1
- CVE-2023-21407: Broken access control (CWE-284), CVSS 3.1 Base Score: 8.8 (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H)
- CVE-2023-21408: Unsafe credentials handling (CWE-732, CWE-256), CVSS 3.1 Base Score: 8.4 (CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
- CVE-2023-21409: Unsafe credentials handling (CWE-732, CWE-256), CVSS 3.1 Base Score: 8.4 (CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
- CVE-2023-21410: Improper Neutralisation of Special Elements (‘Command Injection’) (CWE-78), CVSS 3.1 Base Score: 7.2 (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H)
- CVE-2023-21411: Improper Neutralisation of Special Elements (‘Command Injection’) (CWE-78), CVSS 3.1 Base Score: 7.2 (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H)
- CVE-2023-21412: Improper Neutralisation of Special Elements used in an SQL Command (‘SQL Injection’) (CWE-89), CVSS 3.1 Base Score: 7.2 (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H)
The most impactful vulnerabilities are CVE-2023-21408, CVE-2023-21410 and CVE-2023-21412 since these issues can be chained together to allow an attacker with limited viewer privileges to execute arbitrary code as ‘root’ user on the Axis camera hosting the License Plate Verifier application.
CVE-2023-21412: This vulnerability allows an attacker with general viewer privileges for one camera to extract the authentication credentials of a synchronised system (via the ‘camera synchronisation’ feature) through an SQL injection attack in the web interface. This allows a general viewer of one camera to ultimately gain access to a new device and to escalate their privileges to those of an operator.
CVE-2023-21408, CVE-2023-21410: These two vulnerabilities are command injections exploitable by a user authenticated with an operator account, allowing the attacker to execute arbitrary code on the device with ‘root’ privileges.
If at least 2 cameras are synchronised with the dedicated ‘camera synchronisation’ capability offered by the License Plate Verifier application, by chaining CVE-2023-21412 with one between CVE-2023-21408 or CVE-2023-21410 an attacker with a low privileged viewer account could extract a set of valid credentials to escalate their privileges to operator, subsequently executing arbitrary code with ‘root’ privileges on one of the connected Axis cameras.
In addition, viewer access can be set as anonymous by toggling a specific option (not enabled by default), requiring no authentication to visit the web interface as a general viewer. This would eventually allow the described attack vector to be exploited by a completely unauthenticated attacker regardless of assigned user group access.
Vulnerabilities In Axis License Plate Verifier Remediations
Nozomi Networks recommends that asset owners quickly upgrade the Axis License Plate Verifier application described in the Axis Security Bulletin dated 01/08/2023 to prevent any abuse of their systems by unauthorised threat actors. The updated License Plate Verifier application can be manually installed by downloading the latest version from the official Axis Communications webpage or automatically by upgrading the device firmware to the latest release.
“We thank Nozomi Networks for their excellent research and good collaboration throughout the disclosure process,” said Andre Bastert, Axis Product Security Team.
“It is the second time after some work in 2021 that we had the pleasure now to work together with Nozomi Networks and benefited from their expertise.
“Axis Communications welcomes security researchers and ethical hackers to inspect our products and applications as it is our belief that long-term sustainable cyber security is created through collaboration and transparency.”
You can read the relevant Axis Security Bulletin here or read more SEN news here.
“Nozomi Networks Finds Vulnerabilities In Axis License Plate Verifier.”