What is TinyML and what are its security applications?
Security Applications Of TinyML – Tiny Machine Learning is an evolution of traditional machine learning technology in which machine learning is undertaken on low power devices at the edge of cloud applications, not on a central server.
Because of its modest processing demands, TinyML makes machine learning possible on low power sensors or automation devices – including battery powered devices – that are not connected to the internet, but which might link to a controller, or a cloud application.
Security Applications Of TinyML
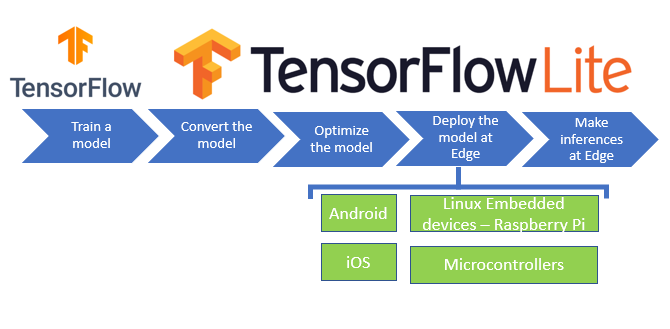
TinyML employs the simple processors of device controllers using models like TensorFlow Lite, which converts 32-bit floating points to 8-bit floating points in the open source TensorFlow deep learning platform so as to trim the weight of machine learning model in multiple ways that enhance processing speed, reduce storage requirements and reduce power demands.
There’s no question that TensorFlow Lite offers pre-trained machine learning models for electronic security applications, including handling object detection in image streams, filtering user behaviour and generating data-informed responses in real time.
Importantly, TensorFlow Lite is not the only option, though it has the benefit of being based on the open source TensorFlow platform. Other capable models include CoreML (Apple) and PyTorch Mobile, which is a lightweight version of Facebooks PyTorch deep learning library.
While TinyML is unquestionably the next thing in IoT, with huge amounts of money being invested in the technology, how it might find its way into electronic security devices and how that information might be communicated to security teams is something for system developers and manufacturers to partner on. There’s unquestionably hunger for more information.
Alarm sensors, which are robust, capable and extremely long lived, have remained more or less static in terms of functional capability for many years. The introduction of imaging sensors to these sensors, and machine learning capabilities in support of pyroelectric, microwave, microphone, vibration, temperature and other integrated sensors could allow single devices to provide much richer situational awareness to security managers.
What are the security applications of TinyML? We think they will revolve around the ability to deliver useful data from huge networks of sensors which are currently untapped and to deliver it ways that inform security operations in real time.
There’s great potential for TinyML to empower new generations of security sensors, enhancing situational awareness and driving forward the automation of event monitoring and reporting.
More news from SEN.
“Security Applications Of TinyML”










Good initiative John. We are having a presentation on a “universal sensor” using TinyML.
I think your article asks “What are the security applications of TinyML?” This might be a malformed question. You have the sense right but it is not the application of TinyML in security it is the use of “analysis” in security. Analysis across the siloes! What TinyML does is builds associations from the data provided to it. Anyway no point explaining it in a text form – I will send you an article.
Thanks for this feedback, Olly – I get what you saying – love to get an article when you can. Cheers.
Interesting Article John. It would be interesting to explore the moral and ethical implications and applications of technologies such as this in light of the upcoming conclusion of the investigation into the use of facial recognition technology in Bunnings, K-Mart and Good Guys, by the Privacy Commissioner.
While we certainly have the ability to create some truly mind-boggling technologies and devices now, the use of these technologies is often not really considered outside of their creation. It would be an interesting and likely controversial topic to explore the ‘how’ of bringing these technologies to market can be ethically achieved.
Agree, Andrew. It seems our tech has vast potential but if applications are not managed carefully and regulated properly to ensure compliance with some mutually agreed ‘best practice’, the future is going to get messy. Coming to an agreement around what best practice looks like will be the trick. Of course, while we agonise about ethics, digital giants will go on siphoning away our every face wrinkle, swipe and mouse click. It’s a conflicting time for us.
Indeed it is a conflicting yet fascinating time for us. Having a conversation around the use of all this new technological capability is almost certainly well worth having. It will be a difficult one to be sure, however the outcome will be a healthier and happier society that isn’t ruled by technology, rather having technology working constructively for it.